Quick intro
BitLocker is like backup. It’s good to have it. It’s better to have the restore verified as well.
If you’re planning to implement BitLocker into your organization (or already have that), it’s good to know what’s the choice of storing the recovery password:
- save to a file – either usb stick or unc share
- backup to ActiveDirectory
- backup to Azure ActiveDirectory
- use MBAM
More information can be found here.
For me, the best approach would be to:
- use GPO to encrypt end user device AND store the password in Active Directory
This can be configured here: Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> BitLocker Drive Encryption -> Store BitLocker recovery information in Acive Directory Domain Services.
This also ensures that encryption won’t start if recovery key failed to be backed up to AD.
- use Intune and encrypt user device AND store the password in Azure Active Directory with self-service key recovery feature
This doesn’t introduce the cost of MBAM or SCCM.
What if you already have your drives encrypted, and now want to improve the process od recovering information? As always – PowerShell to the rescue. To send information to AD we can use Backup-BitLockerKeyProtector. It can accept either KeyProtectorID or the ID itself. Retrieving those is simple.
Ways to get BitLocker recovery key information to AD and Azure AD
Manage-BDE
We can get the information using manage-bde tool:
Retrieve information
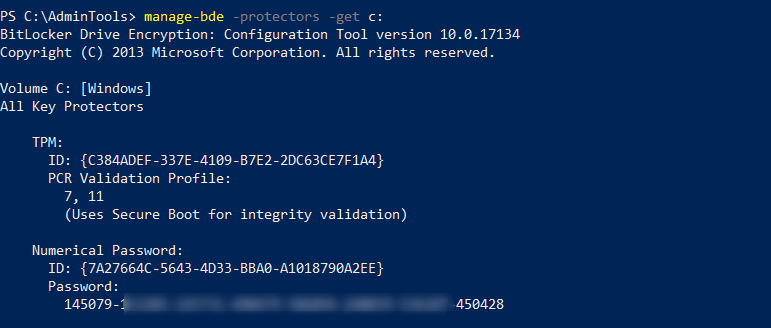 Send to AD
Send to AD
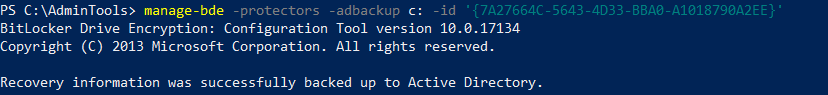
PowerShell
This is more fun (objects) do I’ll describe this. Let’s first get information about our volumes:

As you can see I have only one drive, encrypted with TPM. To get the information we require just select-object
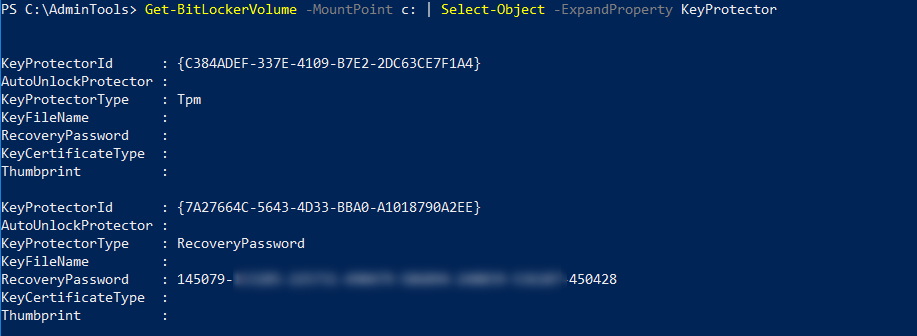
This returns two objects for each drive. We’re interested in the second object
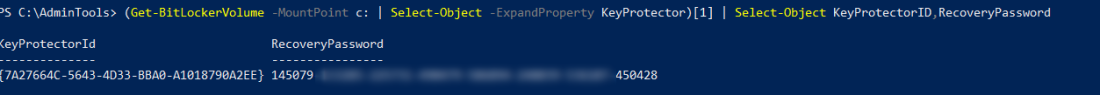
Let’s store the information to ActiveDirectory now:

If I would have more drives, this would come in handy:
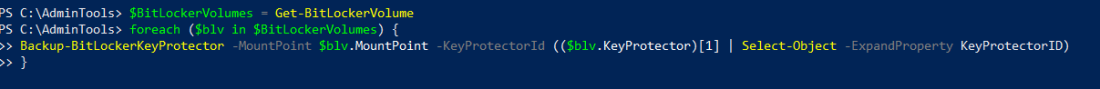
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| $BitLockerVolumes = Get-BitLockerVolume | |
| foreach ($blv in $BitLockerVolumes) { | |
| Backup-BitLockerKeyProtector -MountPoint $blv.MountPoint -KeyProtectorId (($blv.KeyProtector)[1] | Select-Object -ExpandProperty KeyProtectorID) | |
| } | |
| ComputerName: NBMCZERNIAWSKI2 | |
| VolumeType Mount CapacityGB VolumeStatus Encryption KeyProtector AutoUnlock Protection | |
| Point Percentage Enabled Status | |
| ———- —– ———- ———— ———- ———— ———- ———- | |
| OperatingSystem C: 236.22 FullyEncrypted 100 {Tpm, RecoveryPassword} On |
Azure Active Directory
Same goes with sending RecoveryKey to Azure AD, this time with BackupToAAD-BitLockerKeyProtector:

This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| $BitLockerVolumes = Get-BitLockerVolume | |
| foreach ($blv in $BitLockerVolumes) { | |
| BackupToAAD-BitLockerKeyProtector -MountPoint $blv.MountPoint -KeyProtectorId (($blv.KeyProtector)[1] | Select-Object -ExpandProperty KeyProtectorID) | |
| } | |
| ComputerName: NBMCZERNIAWSKI2 | |
| VolumeType Mount CapacityGB VolumeStatus Encryption KeyProtector AutoUnlock Protection | |
| Point Percentage Enabled Status | |
| ———- —– ———- ———— ———- ———— ———- ———- | |
| OperatingSystem C: 236.22 FullyEncrypted 100 {Tpm, RecoveryPassword} On |
Retrieve RecoveryKey
From AD
Now the best part – how to get the information back. Since Windows 2008 BitLocker Recovery Key is stored in AD in msFVE-RecoveryInformation objectclass aassociated to Computer. To get that we first need to get Computer Object and then search Active Directory for ObjecClass of given type. This is assuming your account have rights to read the information from AD in the first place! (great article here)

This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| $ComputerName = 'nbmczerniawski2' | |
| $DNComputer = Get-ADComputer $computerName | Select-Object -ExpandProperty DistinguishedName | |
| $obj = get-adobject -Filter {objectclass -eq 'msFVE-RecoveryInformation'} -SearchBase $DNComputer -Properties 'msFVE-RecoveryPassword' | Select-Object Name,msFVE-RecoveryPassword | |
| [Ordered]@{ | |
| ComputerName = $ComputerName | |
| RecoveryPassword = $obj.'msFVE-RecoveryPassword' | |
| Date = Get-Date -Date ($obj.Name ).Split('{')[0] | |
| KeyID = (($obj.Name ).Split('{')[1]).TrimEnd('}') | |
| } |
I’m using custom objects for better readability. Date shiws when the drive was encrypted, not when the information was backed up.
From Azure AD
There is a delay between using BackupToAAD-BitLockerKeyProtector and the information showing on AzureAD. Give it time to synchronize 🙂
Go to https://myapps.microsoft.com, go to the “Profile” page and see all the registered devices:
From there You can view the recovery password for You devices.
Btw – it’s not very intuitive – You cannot access this informatorom directly from office.com -> profie pages.

hi i need a help plz i lock my D drive to bitlocker and i lost of my both of password or key plz help me how i open to my drive to without bitlocker recovrey key or password
LikeLike
Without key or password you’ll do nothing. If that would be on the same system You could try to unlock it (if keys were in TPM). Else – sorry, but that’s the power of encryption – no key=no data.
LikeLike
and my windows 7
LikeLike
Is there any way to back up the recovery keys using a csv file with the computer names and the recovery Id for each? MS is ending MBAM support so we are trying to see if it is possible to import the keys from a list instead of running a command on each machine (scripted or not)
LikeLike
Not sure about MBAM – didn’t work with this but if You don’t have the keys backed up to AD or AAD You’ll have to invoke to each machine. And best would be to store keys in AD/AAD on addition to an offline copy. You can either use script from this blog or Przemek Klys has a nice one too https://evotec.xyz/backing-up-bitlocker-keys-and-laps-passwords-from-active-directory/
LikeLike
Invoke-Command throws he following error, but running it from the local machine works fine.
The Active Directory Domain Services forest does not contain the required attributes and classes to host BitLocker Drive Encryption or Trusted Platform Module information. Contact your domain administrator to verify that any required BitLocker Active Directory schema extensions have been installed. (Exception from HRESULT: 0x8031000A)
LikeLike
Yea, got that sometimes. That means your AD is not ready to accept BitLocker keys from Computers accounts (it only works if done from AD user with local admin rights). To overcome that you need to delegate AD rights for SELF object to write msTPM-OwnerInformation to descendand Computer Objects. I’ve updated it here here: https://www.mczerniawski.pl/bitlocker/retrieve-bitlocker-recovery-key/#update-2019-04-23
LikeLike
Backing up remotely works now. Thanks for the help
LikeLike
My PS as admin opens to c, system 32. Can’t cd to admin tools, not found. Cmd you posted doesn’t work.i can run it, no errors, but nothing onscreen.
PS: Wish people who write these great articles would place the code outside of the image making it accessible for copy and paste.
LikeLike
The page/code has been moved to https://www.mczerniawski.pl/bitlocker/retrieve-bitlocker-recovery-key/
You need to have AdminTools folder on your C drive created or… move to any other folder. Copying and running scripts from the internet directly may be.. dangerous sometimes. It’s good to review them first:).
As for the code – apart from images I’ve also posted code as github gists – from which you can copy those. So code you should be able to run – is in gists. Few first are just to demonstrate/show output.
Also – this is an old article – I was still learning the platform back then. Since then I tend to get the code directly on the page as code blocks.:)
Thanks for the comment 🙂
LikeLike
Thank you for the script that backs up keys from multiple drives to AAD!
LikeLike
I have the following problem.
I have activated bitlocker via powershell on one of our computers.
A external hard disk was connected to this computer via usb.
In the powershellscript after the encryption process the key is stored in our active directory. However, the gpo for external usb devices to store the key in the active direcotry was not yet active only for systemdrive and fixed data drives. Now the external hard drive is encrypted and the key was in the powershellsession which was of course closed via software distribution or was not visible.
I wonder how windows allows it at all on an external hard drive the key nowhere to store also not in the azure ad.
Where I have looked everywhere:
Active directory
Azure ad
His private ms account
This is the output of the cmd
Volume “F:” [The name is unknown].
All key protections
Numeric password:
ID: {1250ECFE-85BB-41F1-ADAA-5B8A41B6XXXX}
External key:
ID: {FA6D25F3-80E0-468C-95FE-93C2B15DXXXX}
External key file name:
FA6D25F3-80E0-468C-95FE-93C2B15XXXX.BEK
I have slowly tried everything possible that is in my competence.
Is there possibly another possibility?
LikeLike
They key is stored in TPM for internal use. The AD/AzureAD is just a backup of those keys in case you need to attach the external drive to another machine (if that’s what you’ve configured in your GPO).
If the drive was encrypted without storing keys in TPM, and you have no keys, then basically the drive is.. ready for formatting ;(
LikeLike
Thanks for your quick answer.
I have gpo enabled at this time unfortunately only for “fixed data drives” and “operating system drives” but not for removable data drives.
I have the computer where the script was executed at this time and the hard disk.
Here is an excerpt from powershell:
MountPoint : F:
EncryptionMethod : XtsAes128
AutoUnlockEnabled : False
AutoUnlockKeyStored :
MetadataVersion : 2
VolumeStatus :
ProtectionStatus : Unknown
LockStatus : Locked
EncryptionPercentage :
WipePercentage :
VolumeType : Data
CapacityGB : 0
KeyProtector : {RecoveryPassword, ExternalKey}
so you think the disk is lost or … ?
LikeLike
I’d say so. Look at the last line – there’s KeyProtector with RecoveryPassword and ExternalKey). This is how it looks when it’s with TPM:
KeyProtector
————
{Tpm, RecoveryPassword, RecoveryPassword, RecoveryPassword…}
So… I’d say its toasted
LikeLike